Mobile Application
Penetration Testing
Your Application Security Experts
Your Application Security Experts
Annually conducted for clients
Discovered last year alone
Powered by Proven Methodologies
Our consultants conduct our Mobile Application Penetration Tests in accordance to the OWASP Mobile Application Security Testing Guide (MASTG) and the OWASP Mobile Application Security Verification Standard (MASVS):
- MASVS-STORAGE: Secure storage of sensitive data on a device (data-at-rest)
- MASVS-CRYPTO: Cryptographic functionality used to protect sensitive data
- MASVS-AUTH: Authentication and authorisation mechanisms used by the mobile app
- MASVS-NETWORK: Secure network communication between the mobile app and remote endpoints (data-in-transit)
- MASVS-PLATFORM: Secure interaction with the underlying mobile platform and other installed apps
- MASVS-CODE: Security best practices for data processing and keeping the app up to date
- MASVS-RESILIENCE: Resilience to reverse engineering and tampering attempts
- MASVS-PRIVACY: Privacy controls to protect user privacy
Depending on the nature of the application, we tailor testing depth according to the MASVS levels as shown below:
MAS-L1 - Essential Security
MAS-L1 establishes foundational security requirements that all mobile apps should follow. This profile focuses on secure default settings and widely recognised essential security measures. MAS-L1 is recommended as a baseline for all mobile apps.
MAS-L2 - Advanced Security
Building on MAS-L1, MAS-L2 adds extra security measures and best practices to address more advanced threats. It requires a more thorough approach to threat modelling and testing strategies. This profile is recommended for apps that handle high-risk sensitive data or include critical functionality.
MAS-R - Resilient Security
MAS-R focuses on preventing attackers from extracting intellectual property, bypassing security controls, or disrupting the ecosystem. The security measures were intended to strengthen resilience against client-side threats. This profile is recommended for apps that need to protect valuable business assets and logic. Secure communication channels against interception and tampering.
To Help You Meet Your Unique Industry, Compliance, and Technical Requirements For Web Security
Velocity, our proprietary compliance, standards, and service delivery platform, comes pre-loaded with over 20,000 test cases designed to address 200+ industry standards, regulatory frameworks, and technical specifications.
Every consultant tests from the same set of comprehensive standards, ensuring consistent quality across all teams.
We ensure compliance across different markets and sectors, so you don't need to decode complex regional requirements or delay launches - we can already do that for you.
Test Case Coverage:
OWASP MASTG Android
OWASP MASTG iOS
RASP
Regional Privacy Standards
Hardening Your Systems Using Proven Security Frameworks
Velocity, our proprietary compliance, standards, and service delivery platform, comes pre-loaded with over 20,000 test cases designed to address 200+ industry standards, regulatory frameworks, and technical specifications.
- Every consultant tests from the same set of comprehensive standards, ensuring consistent quality across all teams.
- We ensure compliance across different markets and sectors, so you don’t need to decode complex regional requirements or delay launches – we can already do that for you.
Test Case Coverage:
OWASP MASTG Android
OWASP MASTG iOS
RASP
Regional Privacy Standards
Actionable Recommendations You Can Bring To Stakeholders
We deliver comprehensive, cryptographically signed penetration testing reports that are both verifiable and tamper-proof. Each report includes detailed vulnerability backgrounds, clear impact assessments, and actionable recommendations. And because security is a global concern, our reports are available in 113 languages—ensuring your cross-border teams are always in the know.
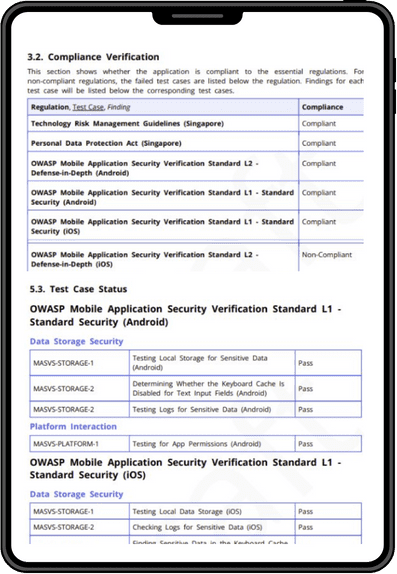
Compliance Verification Reporting
The report clearly shows the specific standards the app complies to.
Detailed down to the Test Cases

Detailed Background
We explain the vulnerability clear enough for technical and non technical stakeholders to understand.
Impact statements
Explaining the business impact of the vulnerability.
Recommendations
Actionable insights stakeholders can take to remediate gaps.
And We’re Just Getting Started…
We believe in delivering long term application security. That’s why we’re giving you and option to automate your penetration tests with our proprietary service delivery platform, Velocity. Our extensive library of 20,000+ test cases streamlines compliance efforts and eliminates the hassle of new security proposals.
SPEAK TO AN EXPERT
Get Expert Security Guidance,
Book Your Call Now.
Experts in Penetration Testing
Specialists in AppSec
More than 80,000 hours of yearly pentesting
Investment In Innovation and IP Development
Rigorous quality Assurance with Velocity
Other CREST Approved Penetration Testing Services
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Network
We secure your network infrastructure by identifying misconfigurations, weak protocols, and access control flaws across routers, switches, servers, and endpoints. We ensure compliance to many industry standards.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.
Other CREST Approved Penetration Testing Services
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Network
We secure your network infrastructure by identifying misconfigurations, weak protocols, and access control flaws across routers, switches, servers, and endpoints. We ensure compliance to many industry standards.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.

