Cloud Compliance Assessments
Cloud compliance assessments involve a thorough evaluation of your organisation's cloud environment, infrastructure, and operational practices in order to meet the specific regulatory, industry, and internal compliance standards relevant to your business.
Cloud Compliance Assessments
Cloud compliance assessments involve a thorough evaluation of your organisation's cloud environment, infrastructure, and operational practices in order to meet the specific regulatory, industry, and internal compliance standards relevant to your business.
If My Data Is On A Cloud, Do I Still Need To Ensure It Is Secure?
Many organizations assume that moving to the cloud means their data is secure, but this reflects a fundamental misunderstanding of the shared responsibility model.
Cloud providers secure the infrastructure (the “cloud itself”), but they make it clear that the client is still responsible for securing their own data, applications, configurations, access controls, and how the cloud services are used. Misconfigurations, weak access policies, and poor application security remain your responsibility.
What Happens During A Cloud Compliance Assessment?
Vulnerability Assessment
An automated vulnerability scan on the cloud services will be done, followed by triaging and validation of the reported issues.
As cloud resources are not usually publicly accessible, a user account with auditor or equivalent rights to query IAM permissions and service settings is required to help us evaluate the platform for insecure privilege assignment and service misconfigurations which could present potential avenues for attacks.
Prioritisation
If Penetration Testing is in scope, our consultants will prioritise and select from the vulnerabilities discovered to perform further testing.
High impact issues (e.g. public S3 or blob storage, low-privileged user granted with access to sensitive resources or data) will be given priority for exploitation to determine the risk.
Penetration Test
Our consultants will then attempt to verify the existence of these vulnerabilities and exploit them to gain unauthorised access to target systems, user accounts or data. Where permitted and feasible, we will also attempt to escalate privileges and move laterally within both the current cloud environment and ad any connected environments (e.g., on-premises systems, other cloud platforms or SaaS services).
Actionable Recommendations You Can Bring To Stakeholders
We deliver comprehensive, cryptographically signed penetration testing reports that are both verifiable and tamper-proof. Each report includes detailed vulnerability backgrounds, clear impact assessments, and actionable recommendations. And because security is a global concern, our reports are available in 113 languages—ensuring your cross-border teams are always in the know.
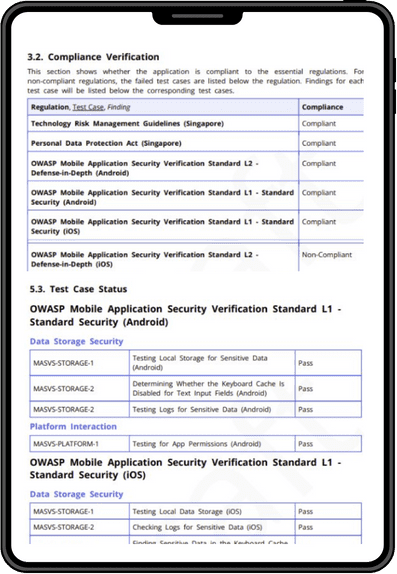
Compliance Verification Reporting
The report clearly shows the specific standards the app complies to.
Detailed down to the Test Cases

Detailed Background
We explain the vulnerability clear enough for technical and non technical stakeholders to understand.
Impact statements
Explaining the business impact of the vulnerability.
Recommendations
Actionable insights stakeholders can take to remediate gaps.




